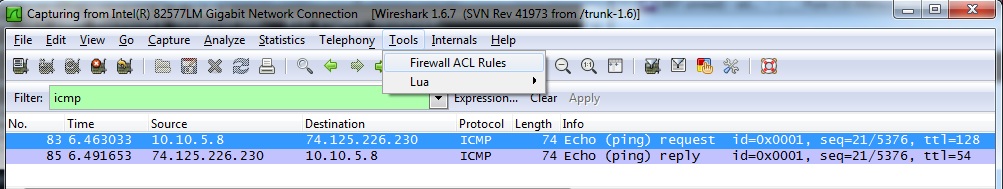
I stumbled onto this wireshark feature by accident really but thought I would share a little bit about it. Essentially what wireshark does is allows you to review all the captured packets and then a single packet in more detail. To create an ACL entry simply select a packet you would like to either allow or deny in an ACL. Now, open the “Tools” menus and select the “Firewall ACL Rules” option.
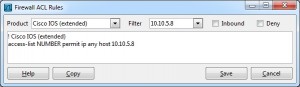
You will see a screen similar to the one below. The default is to deny the source host address from the packet. Switch to the Cisco extended ACL and you can specify source, destination and some more details form the packet in the ACL rule. Reversing the source and destination is also possible by checking / unchecking the “Inbound” box.
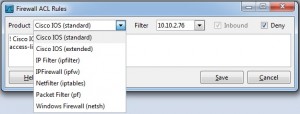
Aside from Cisco Wireshark also supports the common firewall configuration directives for Linux, BSD and Windows just to name a few. The result makes CLI additions to your configuration easy.
While I would probably not personally create Cisco rules this way learning a new system might be nicer with this option. To improve on this feature I would say a multiple packet to multiple line configuration option would be nice.