Working in a large environment with 100% power availability as a requirement I have had the experience of working with many APC UPS systems. We typically monitor the UPS remotely and from time to time have to log in to check statuses or review errors. Our environment frowns upon shared credentials as do I so authentication to these systems had to be updated. I knew we had options because I had seen RADIUS authentication listed in the specifications for the management card.
Initially I created a fairly vanilla policy and was able to log into the APC’s. The issue, however, was that the access level I received was a read only level. To fully administer the unit there was something else that had to be returned to the unit via radius. After some serious searching and experimentation through the documentation I found the answer.
First, be sure your APC unit is defined as a client in NPS. Next, create a network policy to process the authentication request. My policy was configured as follows:
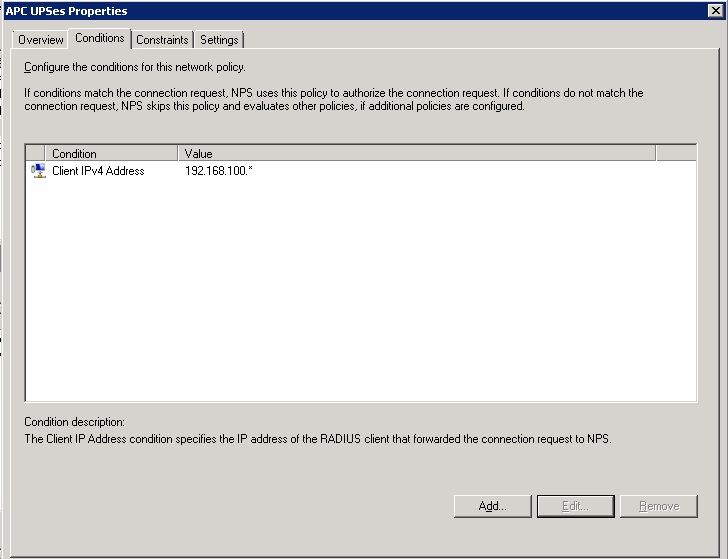
- First, I filter I would add some items under the conditions tab. For me setup I limited the IP addresses that connections could come from with the “Client IPv4 Address” option. You will also have to add a “Windows Group” to control the users who have access.
- Under the “Constraints” tab I selected “PAP” authentication since that is all the APC supports.

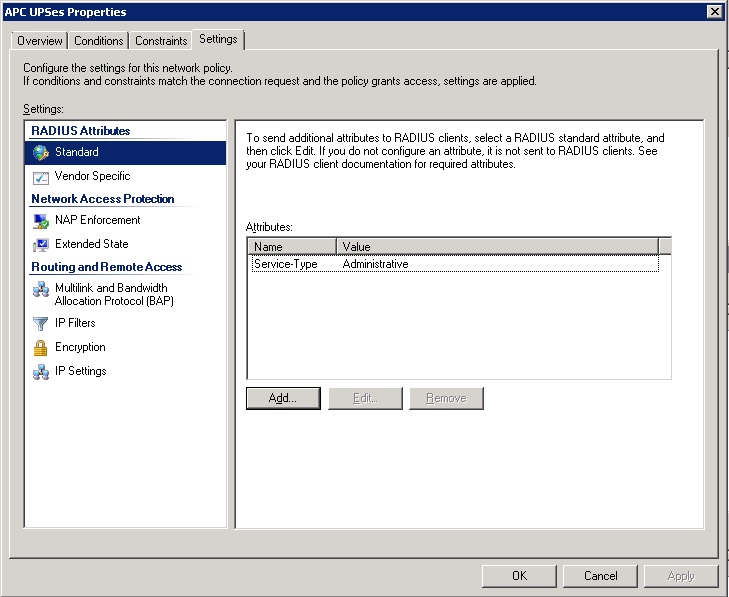
- Under the “Settings” tab we can configure the settings that get sent back to the Radius client. In this case, the APC UPS. We will want to use the “Service-Type” attribute and will want to set its values to “Administrative” to allow full administrator access or to “login” to allow only limited read only access.
Assuming your Radius Client is added correctly to NPS, and the client its self is pointing to the Radius server you should now be able to authenticate.
One downfall to this setup is that you cannot log in as the “apc” username while Radius is configured. Be aware of this! The best option I have for getting back into the APC unit with the local username while Radius is enabled is to disable the UPS’s corresponding Radius client in the NPS server configuration.
I Hope this was helpful to someone!

14 Responses to Authenticating APC Network Management Cards with Network Policy Server