If you have listened to anything IT in the past five plus years you have probably heard of and experienced the “virtualization” buzz word. Typically, it’s referencing host or server virtualization as this is the most common and well known. There are, however, other instances where virtualization of sorts can be used to break hardware into isolated network building blocks. Virtual Routing and Forwarding instances (VRFs) on Cisco routing devices are one such example.
Simply put a router forwards packets based on a routing table. The routing table is the key piece to any routing decision. Any packet that is processed by a router is forwarded based on that table. Different routers have different tables and do different things with the packets they receive. While the entire router operating system is not virtualized with VRFs the routing tables are. This allows various routing tables to run within the same device effectively making the device function as if it where two separate devices; basically. Cisco depicts this in their network design guide like this:
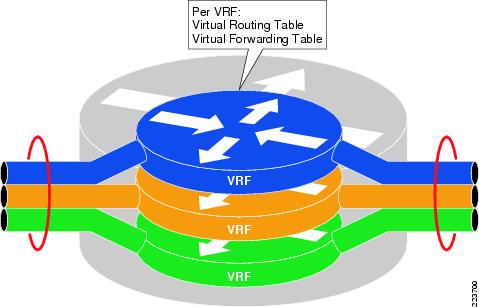
VRFs are to Layer 3 what VLANs are to layer 2. They provide a fully isolated network path. Nothing can map from one to the other without the administrator creating a link. VRFs are most common in service providers MPLS networks to isolate different customers. They also can have a roll in corporate networks as well in the form of VRF-lite. Let’s look at a sample deployment scenario: You have two internet connections, one for guest users and one for corporate users. Each is required to be completely isolated from the other. You have VLANs to separate these two classes of users within your network as well. Your network has grown to the point of needing routing inside the corporate network. Enter VRFs. Let’s look at the design in the image below:
The Blue lines indicate our corporate network while Red is the guest network. Each has its own path to the internet despite the fact common hardware is in use. Now, let’s get our feet wet with a little configuration on the command line interface with some sample configuration and diagnostic commands.
First setup the router and create a VRF called “guest”.
R1(config)#ip vrf guest R1(config-vrf)#exit
Now, let’s get the router configured with some networks as we typically would. These addresses will show in the global routing table as per the “show ip route” command.
R1(config)#interface FastEthernet0/0 R1(config-if)# ip address 192.168.1.1 255.255.255.0 R1(config-if)#interface FastEthernet1/0 R1(config-if)# ip address 10.10.10.1 255.255.0.0
Jump back and check the routing table:
R1#sh ip route Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route 10.0.0.0/16 is subnetted, 1 subnets C 10.10.0.0 is directly connected, FastEthernet1/0 C 192.168.1.0/24 is directly connected, FastEthernet0/0
Looks normal right? Ok, it’s time to implement the VRF on some interfaces.
R1(config)#interface FastEthernet0/0.100 R1(config-subif)# encapsulation dot1Q 100 R1(config-subif)# ip vrf forwarding guest R1(config-subif)# ip address 192.168.1.1 255.255.255.0 R1(config-subif)#interface FastEthernet1/0.200 R1(config-subif)# encapsulation dot1Q 200 R1(config-subif)# ip vrf forwarding guest R1(config-subif)# ip address 192.168.2.1 255.255.255.0 R1(config-subif)#exit R1(config)#
You are probably saying to yourself “HEY! He just used an IP address thats already in use!”. This is allowable but maybe not as recommended… Like I said the tables are completely separated. Another word of caution I have to throw in: Interface IP information is cleared when the interfaces VRF membership changes. If you want to move an existing interface into a VRF you will need to be prepared to re assign its IP address.
Let’s compare the global routing table to the guest VRF table.
R1#show ip route vrf guest Routing Table: guest Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route C 192.168.1.0/24 is directly connected, FastEthernet0/0.100 C 192.168.2.0/24 is directly connected, FastEthernet1/0.200
There is very little that has changed. One thing to notice, however, is that the VRF name appears close to the top as “Routing Table: guest”. Again, you will notice the overlapping address space works and is listed in our table.
Another very common task it to install a default route in our routing tables. Lets do this in each of the tables we have here.
R1(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.2 R1(config)# ip route vrf guest 0.0.0.0 0.0.0.0 192.168.1.2
As a final point I would like to make you aware of the different ways to locate information pertaining to each VRF. Since individual interfaces (physical or logical) are bound to VRFs we have to be aware of this when trouble shooting. For instance, if you would like to ping within a particular VRF its best to be specific, using the “?” if you need any context help. You will notice below the same ping command with or without vrf specified will yield different results:
R1#ping ? WORD Ping destination address or hostname clns CLNS echo ip IP echo ipv6 IPv6 echo srb srb echo tag Tag encapsulated IP echo vrf Select VPN routing instance R1#ping 10.10.10.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.10.10.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms R1#ping vrf guest 10.10.10.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.10.10.1, timeout is 2 seconds: ..... Success rate is 0 percent (0/5)
Also, if you are searching for MAC address information the VRF variant of the command will be needed as well:
R1#show ip arp ? Async Async interface BVI Bridge-Group Virtual Interface CDMA-Ix CDMA Ix interface CTunnel CTunnel interface Dialer Dialer interface FastEthernet FastEthernet IEEE 802.3 H.H.H 48-bit hardware address of ARP entry Hostname or A.B.C.D IP address or hostname of ARP entry Lex Lex interface Loopback Loopback interface MFR Multilink Frame Relay bundle interface Multilink Multilink-group interface Null Null interface Port-channel Ethernet Channel of interfaces Tunnel Tunnel interface Vif PGM Multicast Host interface Virtual-PPP Virtual PPP interface Virtual-Template Virtual Template interface Virtual-TokenRing Virtual TokenRing vrf Show entries for a VPN Routing/Forwarding instance | Output modifiers R1#sh ip arp vrf guest Protocol Address Age (min) Hardware Addr Type Interface Internet 192.168.1.1 - abcd.4444.4444 ARPA FastEthernet0/0.100 Internet 192.168.2.1 - abcd.3333.3333 ARPA FastEthernet1/0.200
I hope these basics are enough to get a you started with VRFs. The basics are just about what you would expect. Routing protocols each have a little bit different way of working in with VRFs. I plan on getting into that in a later article so stay tuned!


5 Responses to Introduction to Virtual Routing and Forwarding (VRFs)