Do you really know what is running in the background on your Windows PC or server? Not knowing is how security holes perpetuate themselves into serious issues. While ignorance may be blissful someone else may be poking around your networking looking for a way in. With Windows systems it’s easy to list listening sockets that could present a risk. Once you know what’s listening on your system you can then hunt down the process and validate its existence. In many cases the services are part of windows or otherwise acceptable services or applications.
To start issue a “netstat” command with the “a”, “n” and “o” options from the command line something like this:
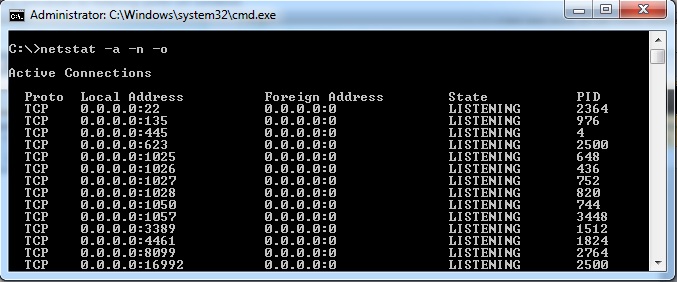
As you can see the local and foreign connection points listed along with the state and process ID for each. In the example above let’s look at the first listening socket. If you know a bit about windows you probably recognize port 22, the typical SSH port, to be out of place. Let’s explore this a bit further to figure out what is listening on this port.
We know the PID associated with the running service is 2364. Let’s get some more information. For this we will use the “tasklist” command. If you do a “tasklist /help” you can get the full list of help options. We want to user the “/svc” option to see services and “/FI” to filter. The filter requires a pattern to filter on so I also include a “PID eq 2364”. The whole command string will look something like this:
 In this example the service turned out to be the FreeFTPdService.exe. You can then google the service if you don’t recognize it. If you do recognize it take note or disable it accordingly. In the case of this example the service is using SFTP on port 22.
In this example the service turned out to be the FreeFTPdService.exe. You can then google the service if you don’t recognize it. If you do recognize it take note or disable it accordingly. In the case of this example the service is using SFTP on port 22.

