Mitel 5000 SMDR Script
The Mitel 5000 is a great system but the base licensed setup has a bit to be desired as far as reporting is concerned. I wanted to know who was making making and receiving calls and how long they were taking. I found some Mitel documentation on how to enable SMDR on the system and sent ahead and enabled it.
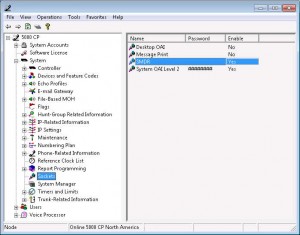
After enabling SMDR on the Mitel (and rebooting it) you can run the script below on a Linux machine to collect live call data from the system. The SMDR data exchange is very simple. If you have any issues with it I suggest looking at the exchange with wireshark to see what is wrong. IO:Socket should take care of everything you need for the TCP connection. The script and phone system do the rest. I suppose this could be turned into a daemon fairly easily and used to log to a database. As always, the sky is the limit…
#!/usr/bin/perl use strict; use IO::Socket; use POSIX; my $host = '1.2.3.4'; # replace with your Mitel's IP address my $port = 4000; my $sock; #variable for connection socket ### Never ending loop while(1){ if($sock){ my $data; $sock->recv($data,86); print $data; undef $data; } else{ $sock = &connect($host, $port); $sock->send(chr(2).chr(0).chr(0).chr(0).chr(132).chr(0)); } #easy now... don't loop so fast... sleep(3); } #Connection to the Mitel system sub connect{ my($host, $port) = @_; #Create Socket my $sock = new IO::Socket::INET( PeerAddr => $host, PeerPort => $port, Proto => "tcp", Type =>SOCK_STREAM) or die "Cannot connect to PBX at address: $host port: $port: $!"; return $sock; } |
Why should we send ASCII character “chr(2).chr(0).chr(0).chr(0).chr(132).chr(0)” to server??
This script was based on packet capture reverse engineering I did on a trial version of another piece of software. Basically I am sending those characters to setup the connection the same way the other piece of software was. You may look into the standards and find that there is a smarter / cleaner way to do it.