As part of a recent network upgrade I was able to get Cisco Prime Infrastructure included in the moneys for the project. I love new systems to play with, of course, and immediately got to work checking out all the bells and whistles. Needless to say, it wasn’t long until I got tired of remembering the root credentials and began looking at RADIUS authentication for some help. Additionally, I’m kind of the security guy too and knew I was breaking my own rules by not having individual user logons in place.
At any rate, I fired up the management console for NPS on the respective windows ’08 box and chopped out a policy. I added my “Net Admins” group from Active Directory and specified the NAS IP address for Prime. Jumping over to Prime I threw my credentials in only to receive an “Invalid Username or Password” message.
I tried again, same thing. I knew my credentials were right so back to the NPS server I went. Sure enough, the logs were actually showing Access Accept messages were being sent back to Prime.
Let me stop for a second and say that before this endeavor I knew only the basics of Radius as it pertains to Cisco but have since gained a significant chunk of knowledge with a lot of guessing and checking to validate it all.
Cisco Prime, like anything IOS, understands most options through Attribute Value Pairs aka “AV-Pairs”. This is actually true for both Radius and TACACS! There are some pairs that are exclusive to TACACS (such as cmd=x and cmd-arg=x) but the majority, including the one I will be discussing here, work without trouble.
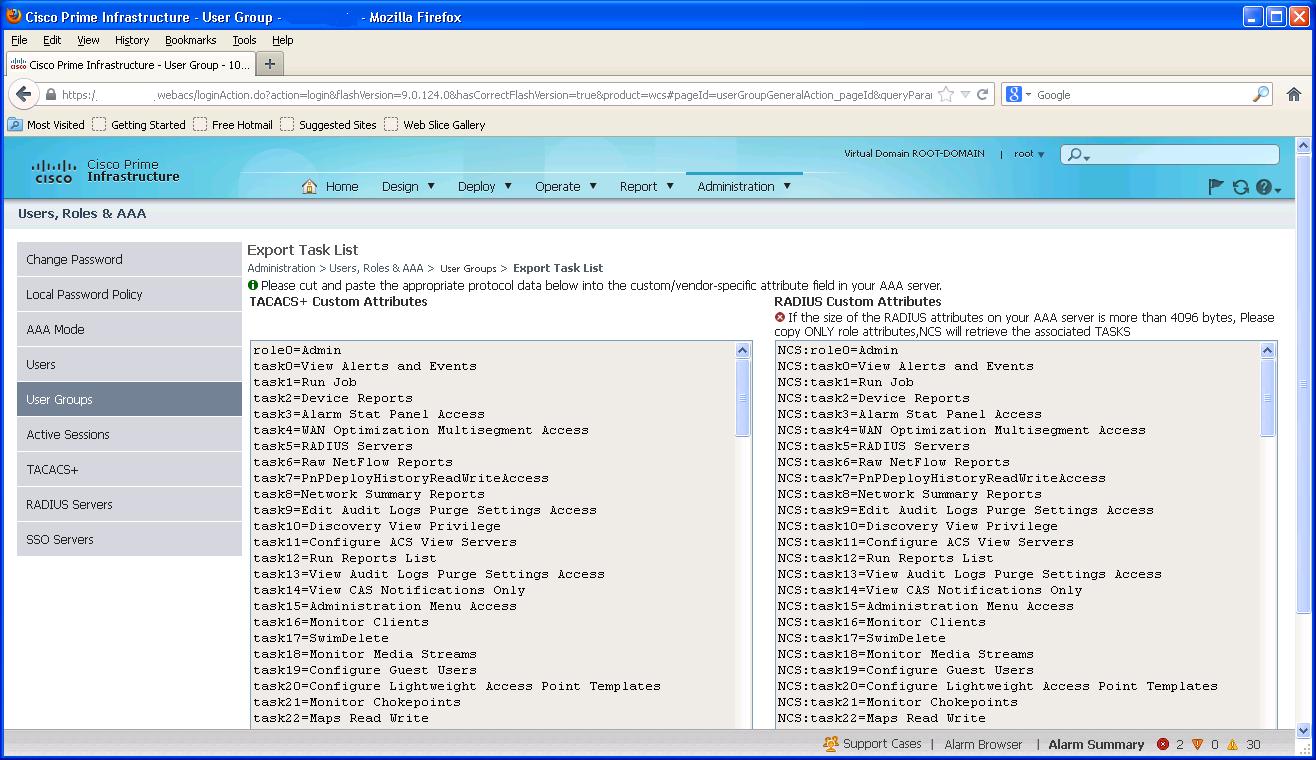
So how does one get the needed AV-Pair information for Prime? Simple, navigate to Administration -> Users, Roles and AAA -> User Groups. Next, click the “Export” button to the right of the group name that has permissions you would like to bestow upon you Radius authenticated user.
Since this article is focused on getting this all to work with the Windows NPS implementation of Radius I want to share another point. Windows cannot send more than 4096 bytes of data in its Radius responses. I know this because I copied all 100 some AV pairs into the configuration only for it to NOT work. That really irritated me to say the least. However, if you’re using a TACACS system of some type you will have to send all AV-Pairs.
At any rate the “role” pair is all that’s needed as the on screen message alludes to.
I added this information to my policy and it STILL didn’t work. I’ll be honest; by this point I had a TAC case wide open with Cisco and the emails where flowing but the actual answer to the problem wasn’t. Finally, as if it was common knowledge from the first few pages of the manually, the technician asks if I had specified the Virtual Domain AV-Pair. Of course, the answer was no.
The million dollar string was something like this:
NCS:virtual-domain0=ROOT-DOMAIN
I added this to the NPS config and finally; it worked!
To circle back around the NPS setup uses the Vendor Specific AV-Pair option as you can see in the screen shot below.
I won’t go into the other details of the configuration here but if you have questions feel free to let me know.
I also wanted to include some documents that pertain to this quest that I found helpful:
1. http://www.cisco.com/en/US/docs/ios/sec_user_services/configuration/guide/sec_rad_ov_ietf_attr.html
2. http://www.cisco.com/en/US/docs/ios/12_2/security/configuration/guide/scftacat.pdf
3. http://www.cisco.com/en/US/docs/wireless/prime_infrastructure/1.3/configuration/guide/pi_13_cg.pdf



5 Responses to Windows NPS Radius Authentication of Cisco Prime Infrastructure